Linux installed on Android devicesColonelAny file has been found to be overwritten. You can overwrite files that require root privileges.Privilege promotionIt’s very effective because it can be done.
The Dirty Pipe Vulnerability – The Dirty Pipe Vulnerability Documentation
https://dirtypipe.cm4all.com/
Named “Dirty Pipe (CVE-2022-0847)”, this vulnerability is responsible for the communication of multiple programs on Linux.PipeIt is said to be the cause. In Linux, once a read file is stored in memory as a cache, it reads faster when re-accessed.Page cacheHowever, with the use of dirty pipe, any area of the page cache can be freely overwritten by the pipe.
With this damage alone, the target of the attack is only the cache in the memory, so the original file can be attacked without leaving a trace because it is not overwritten, and it is a CD-ROM-like read-only because of the cache-only transferable nature. It is also possible to overwrite the data of. With this cache rewrite, it is possible to illegally create an SSH key or create a user and grant root privileges.
The Linux kernel code has a fundamental problem, so there is no solution other than updating to a specific version of Linux. This vulnerability was reported to the Kernel Security Team on February 20, 2022, and was resolved in a February 23 update. The updated version numbers are “5.16.11”, “5.15.25” and “5.10.102”. However, version 5.8 of the Linux kernel code states that this vulnerability exists, so if you are using an earlier version than 5.8, you do not need to take any action.
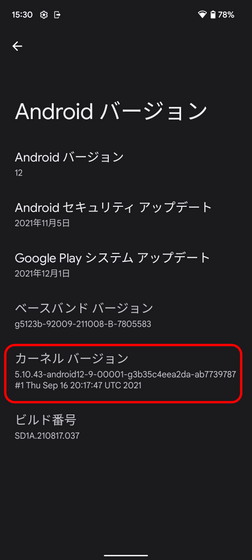
This vulnerability also affects Android using Linux. Google on February 24thMerge the patch into the Android kernelDone. Check “Kernel version” from “Settings” -> “Device info” -> “Android version” to see if your Android device has this vulnerability. If this version is less than 5.8, there is no problem, but if it is a 5.10 series, if the third number is less than 102, if the third number in the 5.15 series is less than 25, and the 5.16 series is below 11 there is a risk. If so, it’s risky and needs to be updated. For example, in the image below, the kernel version is “5.10.43” and the third number is “43”, so it can be said to have this vulnerability.
Max Kellerman, the researcher who identified the risk, provided technical details on the problem, background to the invention, and proof-of-concept code.ReportSummarized in it.
Copy the title and URL of this article
· Related article
30th Anniversary of the World’s Most Used Open Source UNIX Based OS “Linux” – GIGAZINE
What is the internal Linux distribution used by Microsoft? –Gigazine
Inn SecurityPosted by log1d_ts
You can read the machine translated English article Here.

Problem solver. Incurable bacon specialist. Falls down a lot. Coffee maven. Communicator.